
Spear phishing is targeted social engineering: instead of blasting the internet with generic scams, an attacker researches you (role, vendors, projects, travel plans) and sends a highly believable message that nudges you to click, sign, wire, or share credentials. The message might arrive by email, Teams/Slack, SMS, or even a calendar invite, and it often looks like it’s from someone you trust.
What’s changed lately? Two words: context and craft. Criminals pair public breadcrumbs (LinkedIn, vendor portals, press releases) with AI-assisted writing and look-alike infrastructure to produce messages that feel… normal. The bad news: it’s working. The good news: a handful of habits and controls can cut the risk dramatically.
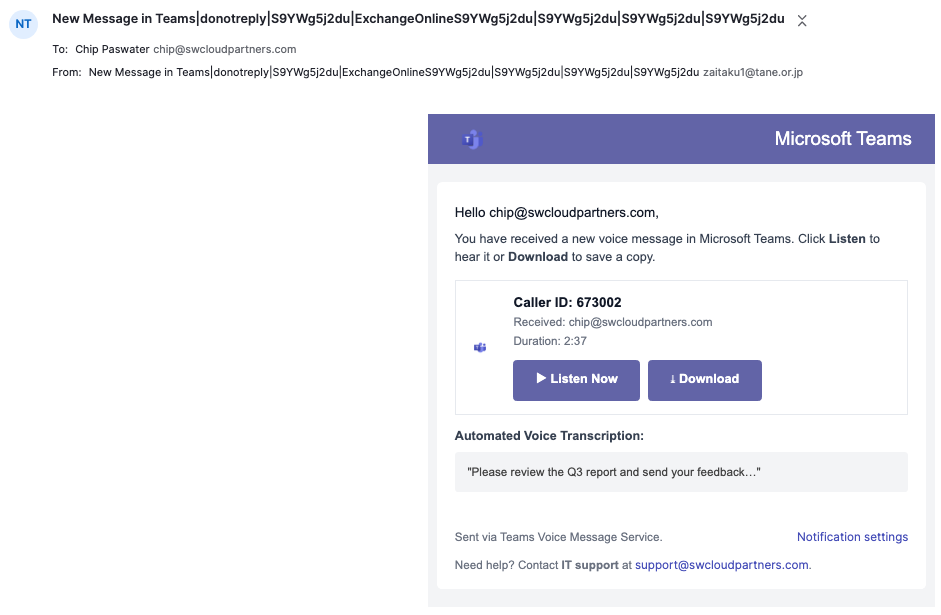
Take a look at this email from Microsoft Teams informing me someone left me a voicemail. I use Teams for meetings and to chat with some of my clients. It has my email address, even my company’s support@ address. Looks legit right? Would you click on this email?
Here is the tell. I do not use Teams for phone calls so I know this is a scam. What makes this a spear phishing attack versus a standard phishing attack is it’s targetted at me with specific information about my business. We are going to see a lot more of these targetted attacks as AI becomes more ubiquitous.
If you look closer at the email there are other clues. No message from Microsoft comes from @tane.or.jp
Southwest Cloud Partners deploys anti-phishing software for our clients as part of our standard Cyber Security baseline which caught and contained this malware.
To understand this better, let’s explore what is a spear phishing attack.
Modern spear phishing tactics
- Thread hijacking – Attackers reply inside a real email thread after compromising a supplier’s mailbox. The link is a malicious “updated document” or invoice.
- Look-alike domains –
acmeco.comvs.acmceo.com, orpay․company.comreplaced withpay-company.com. Fonts and display names hide the trick. - MFA fatigue & push bombing – Flood the user with approval prompts or “confirm your sign-in” messages until one is approved.
- QR phishing (QRishing) – PNG or PDF with a QR code that routes to a fake login page—bypasses URL scanners.
- OAuth consent phishing – Instead of stealing your password, the attacker gets you to authorize a rogue app to your Microsoft/Google account (“needs read mail + send mail” permissions).
- HTML smuggling & “clean” links – Attachments that build malware in the browser, or links that resolve to a payload only after multiple redirects/time delays.
- Voice + email combos – An urgent voicemail or call (sometimes AI-cloned) primes you to expect an email with “wire instructions” or “DocuSign.”
A 5 minute verification framework
- Pause & preview – Hover every link; on mobile, long-press to preview the URL.
- Check the sender – Expand the display name → verify the full address and domain.
- Out-of-band verify – For money, credentials, or document requests, call back using a number you already have saved (not the one in the message).
- Don’t fix their “typo” – Never “confirm” partial SSNs, routing numbers, or 2FA codes.
- Escalate – If it smells off, forward to IT/security. Praise > blame; quick reports save money.
Print this on one page and post it at reception/AP.
What to do if someone clicked (no judgment, just actions)
- Contain – Reset password, revoke sessions, and invalidate OAuth app grants the user may have approved.
- Hunt – Check sent items, forwarding rules, inbox rules (auto-delete, move to archive), and sign-in logs.
- Protect funds – Freeze wires/ACH; call the bank’s fraud desk immediately.
- Comms – Notify the vendor/client if their thread was used; share what you changed.
- Learn – Add the indicators (IPs/domains/hashes) to blocklists; update the training deck with screenshots (redacted).
Your next steps (simple, fast, practical)
- Book a quick review, we’ll run a check of DMARC/MFA/Defender and your approval workflows for payments and vendor banking changes.
- Bring 2–3 suspicious emails; we’ll reverse-engineer them together and turn them into training slides your team will actually remember.
→ Schedule a consult with Southwest Cloud Partners
Las Vegas • Henderson • Boulder City


